Customer Support Request Flooding on Drift
We at IPM are fundamentally interest in how sociotechnical vulnerabilities open the door for bad actors shape organizational behaviors. Sociotechnical vulnerabilities are distinct from technical vulnerabilities in that they leverage social behaviors via technical, automated processes, whereas technical vulnerabilities typically have no, or a greatly reduced, emphasis on social aspects.
Analytics are sociotechnical in that technical information is converted into social action through the interpretation of those analytics. Another great example is the automation of an attack focused on customer support services - can a bad actor force an organization to make decisions by flooding customer service representatives with requests to take certain actions?
As is obvious, organizations are responsive to requests made by users - activist groups like @slpng_giants, as well as the general deplatforming movement we’ve been witnessing the past few months makes the notion that coordinated actors petitioning organizations to make specific decisions about their operation more or less self-evident. Could a bad actor manipulate an organization by mimicking this type of grass-roots behavior? In truth, this sort of automated flooding has already happened on US Government calls for participation - so how much would it cost?
We examined this in terms of a popular service called Drift, which allows for any organization to quickly embed a customer service interaction workflow within an embedded, in-site chat box with only a few lines of code. By targeting this ubiquitous tool, we imagine a scenario in which this attack is rapidly repurposed against many arbitrary organizations using the software. Requests that flow through platforms like Drift are a critical signal for companies to judge customer satisfaction, the status of products and services, and more. This makes it an attractive target for manipulation. We've found that it's straightforward to fake these requests.
A screenshot from within Drift’s administrative panel showing multiple inbound messages from varying locations
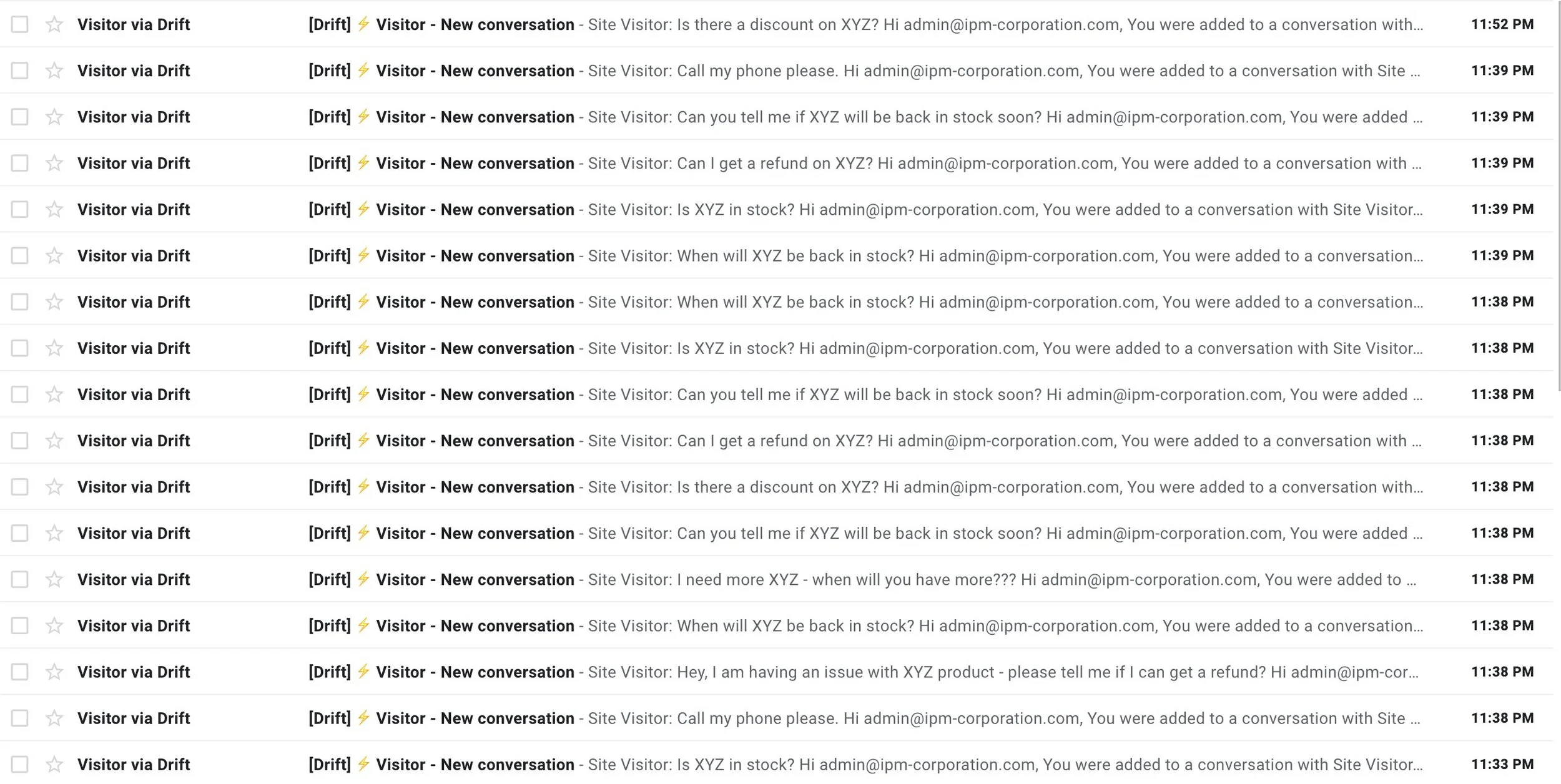
Using our Vulnerability Engine, we determined that for $0.88, it is possible to launch about a ~1,000 phony requests into Drift. One straightforward, brute force attack would be to simply swamp the customer service channel, making it difficult to separate legitimate requests from fake ones. Subtler attacks - shaping company views about what users do and don't want - are also highly economical at this price.
A completely flooded gmail account showing dozens of messages from distinct visitors within the span of several minutes.