Mass Ghost-Carting a Battery on Etsy
As we’ve discussed in previous experiments, in order to work effectively, analytics need to reflect the actual phenomena they intend to measure. If an analytic purports to represent the number of views that a video has received, those need to be real views generated by real humans - not the act of a bot-operated browser sending an HTTP request formulated to merely look like the type of request a person typically sends. Beyond being merely misleading, analytics that are gameable by automated systems can lead to serious consequences.
Etsy is an online marketplace where individuals sell vintage or handmade goods. Like any other online marketplace, sellers are offered access to the market of buyers as well as platform affordances such as payment processing, store analytics, and customer management in exchange for a percent of each sale.
In this experiment, we imagine the consequences of poisoning a buyer’s analytics environment. We envision multiple realistic motivations for such behavior. As with all of our research, we presume financially-incentivized behaviors should be treated as inevitable behaviors. In this experiment, we imagine two types of financially-incentivized actors - first, an actor who is actively attempting to boost their own products, and second, an actor who is attempting to degrade the capacity of sellers selling similar products. In both cases, they utilize the same affordances offered by Etsy - the ability to, without logging in, add a product to a shopping cart.
Under simple circumstances, adding a product to a shopping cart reflects intent to purchase by a buyer. In Etsy, that information is also presented as a call-out on a product so that the seller is aware of this buyer intent, but also so that other shoppers are aware of other buyer intents.
In the case of signaling to the seller, this can create incentives for sellers to proactively prepare for certain types of sales and in the case of signaling to other buyers, this may incentivize FOMO purchases in order to receive a product in limited quantity.
In our example, we created a temporary store, and advertised the first thing we found on our desk as our product for sale:
To induce demand, we set the number of available batteries to only a single battery - we priced it at the minimum possible value, $0.20. We then targeted our store with the IPM Vulnerability Engine, which began to visit the product, click the “Add to cart” button, and then shut down.
We quickly realized that Etsy was not appearing to invalidate Add-to-cart requests initiated on our cloud server IPs, which considerably lowered the cost of our attack, as we did not need to “invest” in a VPN or a Proxy network in order to force the traffic to appear more legitimate.
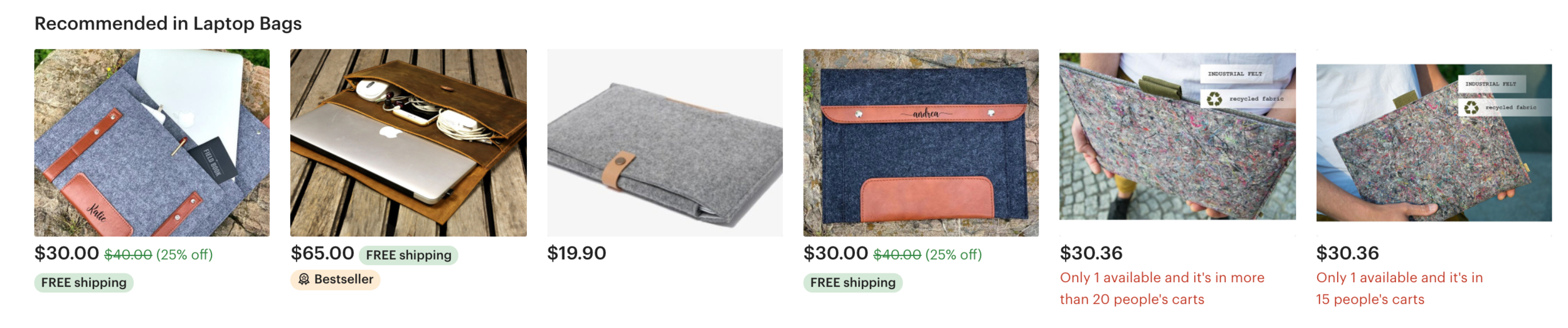
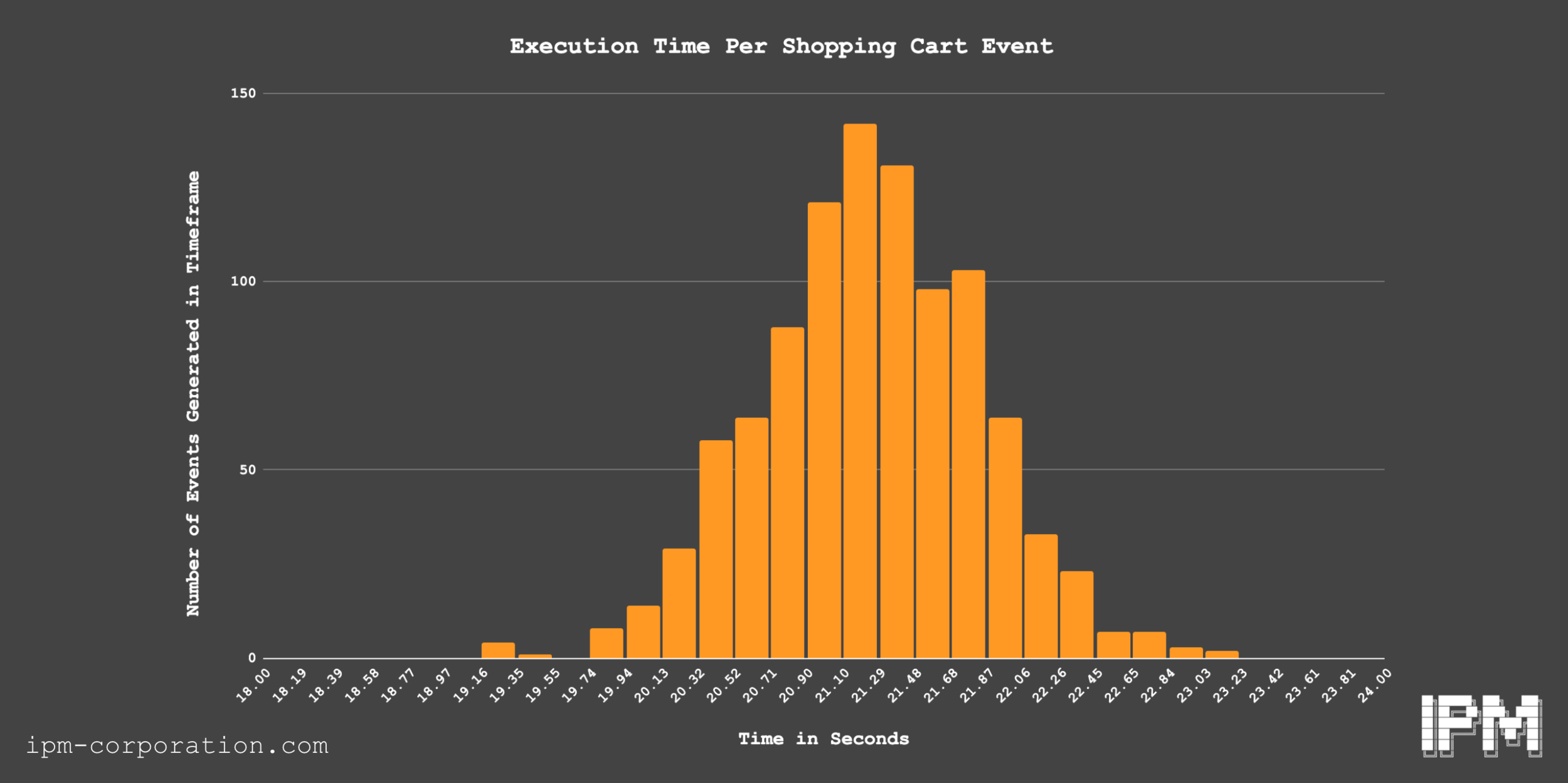
Further, the “Add to cart” button requires no existing account in order for an add-to-cart event being propagated throughout the platform, which minimizes the execution cost and complexity for IPM. As a result, the IPM Vulnerability Engine was able to determine that at a per-unit cost of ≈$0.0005 and a time cost of ≈20 seconds, an add-to-cart event is easily automated. We ran a total of approximately 3,000 add-to-cart events on our battery. After 20 add-to-cart-events, the add-to-cart count publicly displayed alongside the product simply reads as “more than 20” instead of the count we generated.
The analytics page presented to sellers persistently reflects these fraudulent views, which in one version of this hypothetical attack could mislead a seller to believe that their products are sought-after when they in fact are not.
Far from a ginned-up example, a solution looking for a problem, there’s lengthy discussion of nearly identical analytics failures between sellers on Etsy’s community discussion boards. Just a few quotes from these users make clear that the potential for decisions to be made by sellers by these metrics are real:
Same thing happened to me. I have one item that almost 20 people added to cart and today it's all gone. I was very upset about that, wondering why people stop liking it.
I had "over 20 people have this item in your cart" on 8 items this morning. All were gone in one moment of refreshing my shop. I don't believe everyone unloaded their carts at once. Etsy makes no sense and my orders have been nuts this week...which has been a great change.
It creates a pressure on me, to buy more supplies, when I think that over 20 people might want to buy this before Christmas, and I only got supplies for 5.
And then, I have this "over 20 people" under more than one item.
And then, I'm due to Corona[virus] on a small budget...and my supplies take weeks to get here....
so, I just don't know how much I should invest....
Solving this problem requires minimal intervention - Etsy should attempt to block automated browsers, should rate limit the number of add-to-cart events generated by a single IP, and should post-process their analytics to remove fraudulent views. As was shown in our analysis of Youtube, such post-processing is possible - and it may be necessary in this case to keep sellers on the platform.